-
Posts
490 -
Joined
-
Days Won
14
Everything posted by Dunedan
-
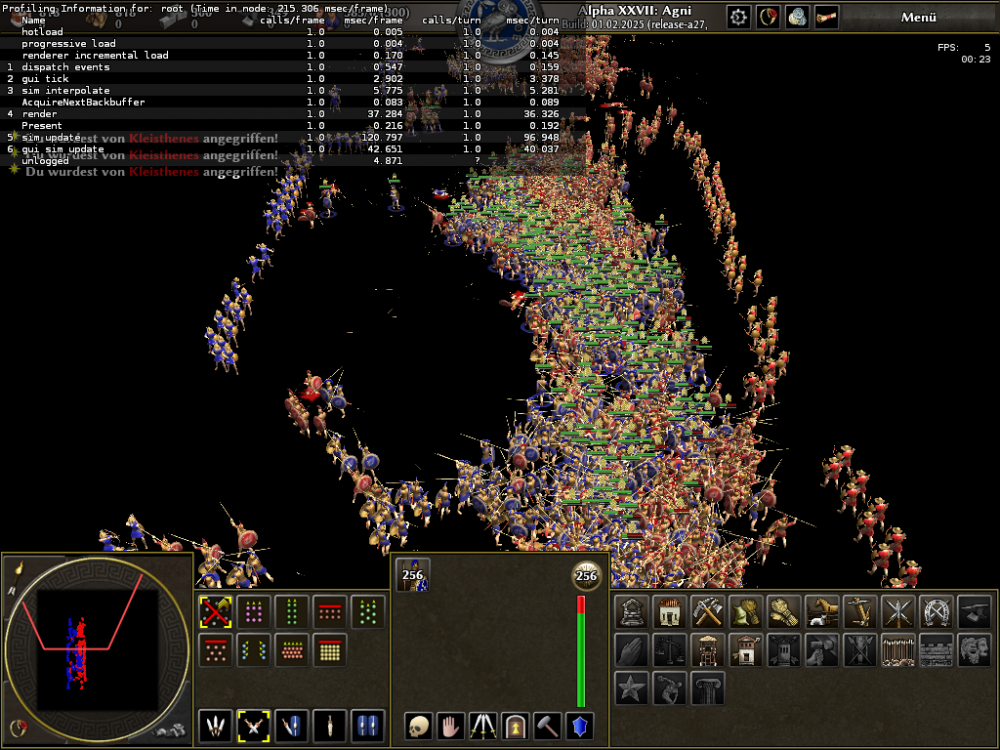
That's a very good example of the problem (kudos for the idea of making a video out of it. so obvious, but nobody did it so far). Just watch the first 20 seconds, when the blue spearmen are moving prior to engaging in the fight. FPS are ~30, but it looks really choppy.
-

How to attract more lobby players?
Dunedan replied to king reza the great's topic in Introductions & Off-Topic Discussion
Get new players to join and let's find out. Our main limitation is https://gitea.wildfiregames.com/0ad/0ad/issues/4203 right now. Without that, there is no real limitation of the number of concurrent players in the lobby, which can't be solved with some additional hardware. -
I've created https://gitea.wildfiregames.com/0ad/0ad/issues/7589 to track this issue.
-

connection refused to server
Dunedan replied to Emacz's topic in Game Development & Technical Discussion
The multiplayer lobby and everything else is back online now. -

connection refused to server
Dunedan replied to Emacz's topic in Game Development & Technical Discussion
Yes, the lobby isn't reachable right now. There are also reports that other WFG-hosted services aren't available for certain people. I'll post an update here as soon as I get one. -
Turns out, while I have a bit more recent hardware, I'm affected by this problem as well. The whole game stutters visibly and frame rates drop very low the more units exist. I'm using a AMD GPU with Wayland on Linux. It doesn't matter whether I run the game with Wayland or XWayland. It doesn't matter whether I select OpenGL or Vulkan as engine. It doesn't matter whether I enable GPU Skinning or not and the problem continues to exist even on lowest graphics settings. What seems to be common from the reports so far is that a lot of time is spent in "sim update", but I'm not sure if that's significant.
-

Rejoining games as spectators instead of player in some cases
Dunedan replied to Dunedan's topic in Bug reports
That's not related to the game itself, but to the connection to the lobby. -

Rejoining games as spectators instead of player in some cases
Dunedan replied to Dunedan's topic in Bug reports
I just changed some config on the lobby server. While that doesn't fix the actual issue, it might speed up the time it takes to work again for affected players. If a player is affected now and rejoins the lobby after 90 seconds, they should have a working state again. There is a slight chance this has a negative effect on players with flaky connections though, which might get disconnected more often from the lobby. Please report your experiences! -

After Ubuntu Upgrade mouse cursor is do not lineup
Dunedan replied to magnitudevector's topic in Help & Feedback
The "0ad" package is available in "oracular-updates" though. -
The lobby is getting updates more or less frequently. This wasn't directly related to Alpha 27 (if you're hinting at that).
-
So here is what happened yesterday: We deploy changes to the lobby using Infrastructure-as-Code (the code for that is available at https://github.com/0ad/lobby-infrastructure/). Applying changes yesterday included a value for an XMPP MUC room option as a boolean (true) in our YAML configuration. That got converted by Ansible into a Python boolean (True) and when applying it to a string (True). As you might notice that changed the capitalization. While ejabberd (the XMPP server we're using) accepted that value, it doesn't support capitalized booleans and hell broke loose when a code path accessing such a configuration option got executed. For one option (like: "ejabberdctl room conference.host logging True") this does cause the XMPP MUC room the option got applied for to get completely deleted immediately. This resulted in the lobby not being available anymore. Debugging what happened took some time. As a workaround we're now passing the configuration values as strings in the first place, which ensures the capitalization stays as desired and doesn't trigger that behavior anymore. I've also opened a bug report for ejabberd, so hopefully it won't be possible in future anymore to set such invalid options: https://github.com/processone/ejabberd/issues/4337.
-
The lobby is back online now. I'll post some details what went wrong later on.
-

Rejoining games as spectators instead of player in some cases
Dunedan replied to Dunedan's topic in Bug reports
The problem tracked here persists for way longer than a minute, sometimes up to an hour or so. -

Rejoining games as spectators instead of player in some cases
Dunedan replied to Dunedan's topic in Bug reports
No report from somebody without a rating yet, so yeah, worth keeping that in mind, even though I believe it's unlikely to be a contributing factor. Who knows, maybe a27 will already fix this issue. -

Rejoining games as spectators instead of player in some cases
Dunedan replied to Dunedan's topic in Bug reports
The issue isn't related to ratings, but caused by the XMPP server seeing two distinct connections from a client. There tend to be more reports from players with rating, as in that case rejoining a game doesn't work. Rating or not is however not related to the underlying issue. -

Questions concerning moderation
Dunedan replied to Atrik's topic in Introductions & Off-Topic Discussion
While I'm not aware of this specific case, feel free to reach out to me if you're interested in details. I'll do. -

Rejoining games as spectators instead of player in some cases
Dunedan replied to Dunedan's topic in Bug reports
All the cases I've been able to look into so far, including the one from today, didn't involve a changed IP-address. -

Rejoining games as spectators instead of player in some cases
Dunedan replied to Dunedan's topic in Bug reports
I just happened to catch a player while they had the problem and was able to ask some questions: OS: Ubuntu 24.04LTS 0ad installed as snap package no second pyrogenesis process running, as verified via "ps" installed mods: Feldmap and autociv, disabling them didn't help using WiFi at home and landline connection to the ISP Having more of such detailed reports would be helpful, as a pattern might emerge. -

Questions concerning moderation
Dunedan replied to Atrik's topic in Introductions & Off-Topic Discussion
As you've already noted I don't comment publicly on specific cases of moderation. Everybody affected by moderator actions will however get a detailed explanation of what he did wrong when asking for it privately. I can assure you that each and every moderator tries to be as objective as possible. If anybody believes a moderator doesn't follow the rules for moderators as documented in https://wildfiregames.com/forum/topic/121838-moderation-of-multiplayer-lobby-irc-and-forums/, please let me know. Players affected by moderation actions may feel that they are treated unfairly, as they're often not aware of how other players are treated for similar violations of the terms of use. In addition, other players might not be prosecuted for similar violations, because no moderator was made aware of such violations. That's why I can only repeat that it's important to report players which violate the terms of use to one of the moderators! There are also players which will use the missing public reaction from moderators to claim they're being treated unfairly, while knowing that they're not. How violations of the terms of use are sanctioned depends on the severity of the violation and the number of violations the player already made in the past. For example for first time violations of low severity a verbal warning or a short mute might be issued, while repeated violations or violations with a high severity might be sanctioned more extensively. If players decide to continue to violate the terms of use over and over, without showing any will to improve, we might even need to issue a complete ban from our services. That's a situation we try to avoid, but unfortunately sometimes have to take to foster a healthy community. Usually that only happens after a moderator talked multiple times with the offending player, tried to explain why their behavior violates the terms of use and tries to get them to change it. (That's of course only possible if the offending player is willing to talk.) Our goal after all is to have a welcoming community and that only works if certain behavior isn't tolerated. -
I won't go into detail regarding the issue with Geriatrix, but rest assured that I have a quite different view on the situation than he has. Rules are enforced equally, so if you believe somebody is breaking the terms of use and isn't held accountable for that, please report it. Moderators don't see everything, so we rely on reports by players as well.
-
My stance would be: less quantity, more quality. As of Alpha 27 0ad will ship with 157 (!) maps. While I believe a big map pool is good, 157 is too much in my opinion. I'd prefer something like ~100 maps in the base game. An easy step to decrease the number of maps would be to eliminate duplicates. For example there are three "Azure Coast" maps and three "Corinthian Isthmus"/"Isthmus of Corinth" maps right now.
-
Please keep it civil in here and focus on the overall issue, not individual players. Otherwise, I'm going to lock this thread.
-

On the usage of AI to generate 0 A.D. content
Dunedan replied to wowgetoffyourcellphone's topic in Official tasks
That 2.9Wh is only for inference and does exclude the vast amount of energy, which is required to train the models. Thanks to "AI" a nuclear power plant is re-opening for Microsoft (https://edition.cnn.com/2024/09/20/energy/three-mile-island-microsoft-ai/index.html) and Google's emissions are growing, instead of going down as they planned (https://apnews.com/article/climate-google-environmental-report-greenhouse-gases-emissions-3ccf95b9125831d66e676e811ece8a18), to just name two examples. -
Fair point. I took the liberty to rename the thread to "The toxic player Issue".
-
This is a gentle reminder that this thread is to discuss the overall issue and not issues with individual players.