-
Posts
446 -
Joined
-
Days Won
13
Everything posted by Dunedan
-
What I'd like to see would be an AI whose difficulty doesn't depend on cheating, like it's the case with Petra AI and its resource multiplier.
-
As 0ad is Open Source everybody can contribute changes. So we'd be happy about pull requests improving AI as well.
-

Rejoining games as spectators instead of player in some cases
Dunedan replied to Dunedan's topic in Bug reports
So how is the status of this bug with Alpha 27? Does is still happen? -
Please report stuff like that with additional details to one of the lobby moderators via private messages here in the forums.
-
Please report something like that privately next time. Impersonating other users violates the terms of use and such accounts will be swiftly banned. The people behind such accounts are usually known players and risk persecution of their "real" account as well by engaging in impersonation.
-
I know I'm a bit late to this party, but CGNAT shouldn't be the cause for not being able to connect to games hosted by other players. Being behind CGNAT is a cause for not being able to host games, but connecting to existing games should work with CGNAT as well. @Vantha I understand that getting your ISP to switch you from CGNAT to a public IP address solved the issue for you, but I guess there was more to it than just this change. My guess is that your ISP does something like filtering traffic for CGNAT users (for example blocking UDP traffic from "unknown" ports), which isn't there for users without CGNAT.
-

A27: Extreme stuttering and OOS on rejoin
Dunedan replied to Seleucids's topic in Game Development & Technical Discussion
If you release cross-platform software the vast majority of feedback will come from Linux users, even if they're the minority of users. That's because Linux users are on average more tech savy and are used to debugging and opening bug reports. So that alone isn't necessarily an indicator for a Linux specific problem. -
If everybody in a match explicitly agrees to the usage of cheats, I wouldn't consider using them an unfair advantage. From my perspective that'd be fine and similar to a game where the "cheats" setting is enabled. However, I believe that's a pretty rare scenario and not what this thread is about.
-
It's not. It's actually within the game licenses that anybody can mod the game. You can make a circular reasoning with the tos stating that cheating isn't allowed in ranked games. Actually the Terms of Use are very clear that everything which grants unfair advantages isn't allowed in multiplayer games, no matter if they are rated or not:
-

Poll: Merging Autociv features into vanilla
Dunedan replied to guerringuerrin's topic in Game Modification
The minimum screen resolution we support (although with some limitations) is 1024x768 pixels. With that resolution there is pretty much no empty space left over there. Parts of the panel are also used when spectating a game for selecting the player to spec. Also mind that the game should appeal to new and casual players as well, which might get overwhelmed when there is too much information shown there. -
https://gitea.wildfiregames.com/0ad/0ad/issues/4710 would achieve that. Feel free to contribute a patch for that!
-
My guess is that you're using an unsupported version of ejabberd. The easiest way to get a lobby up and running is to follow the instructions here: https://github.com/0ad/lobby-infrastructure/ Alternatively you can also just skip the installation of "mod_ipstamp". In that case hosting without STUN won't work, but this option is being removed for Alpha 28 anyway.
-
For me it happens without formations as well.
-
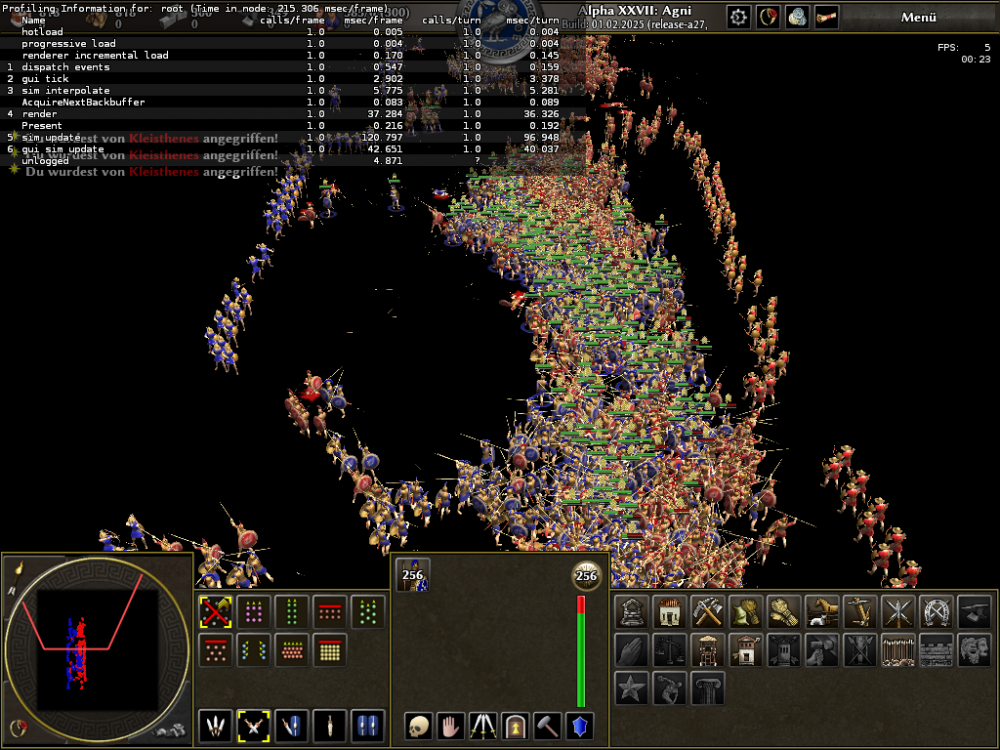
That's a very good example of the problem (kudos for the idea of making a video out of it. so obvious, but nobody did it so far). Just watch the first 20 seconds, when the blue spearmen are moving prior to engaging in the fight. FPS are ~30, but it looks really choppy.
-

How to attract more lobby players?
Dunedan replied to king reza the great's topic in Introductions & Off-Topic Discussion
Get new players to join and let's find out. Our main limitation is https://gitea.wildfiregames.com/0ad/0ad/issues/4203 right now. Without that, there is no real limitation of the number of concurrent players in the lobby, which can't be solved with some additional hardware. -
I've created https://gitea.wildfiregames.com/0ad/0ad/issues/7589 to track this issue.
-

connection refused to server
Dunedan replied to Emacz's topic in Game Development & Technical Discussion
The multiplayer lobby and everything else is back online now. -

connection refused to server
Dunedan replied to Emacz's topic in Game Development & Technical Discussion
Yes, the lobby isn't reachable right now. There are also reports that other WFG-hosted services aren't available for certain people. I'll post an update here as soon as I get one. -
Turns out, while I have a bit more recent hardware, I'm affected by this problem as well. The whole game stutters visibly and frame rates drop very low the more units exist. I'm using a AMD GPU with Wayland on Linux. It doesn't matter whether I run the game with Wayland or XWayland. It doesn't matter whether I select OpenGL or Vulkan as engine. It doesn't matter whether I enable GPU Skinning or not and the problem continues to exist even on lowest graphics settings. What seems to be common from the reports so far is that a lot of time is spent in "sim update", but I'm not sure if that's significant.
-

Rejoining games as spectators instead of player in some cases
Dunedan replied to Dunedan's topic in Bug reports
That's not related to the game itself, but to the connection to the lobby. -

Rejoining games as spectators instead of player in some cases
Dunedan replied to Dunedan's topic in Bug reports
I just changed some config on the lobby server. While that doesn't fix the actual issue, it might speed up the time it takes to work again for affected players. If a player is affected now and rejoins the lobby after 90 seconds, they should have a working state again. There is a slight chance this has a negative effect on players with flaky connections though, which might get disconnected more often from the lobby. Please report your experiences! -

After Ubuntu Upgrade mouse cursor is do not lineup
Dunedan replied to magnitudevector's topic in Help & Feedback
The "0ad" package is available in "oracular-updates" though. -
The lobby is getting updates more or less frequently. This wasn't directly related to Alpha 27 (if you're hinting at that).
-
So here is what happened yesterday: We deploy changes to the lobby using Infrastructure-as-Code (the code for that is available at https://github.com/0ad/lobby-infrastructure/). Applying changes yesterday included a value for an XMPP MUC room option as a boolean (true) in our YAML configuration. That got converted by Ansible into a Python boolean (True) and when applying it to a string (True). As you might notice that changed the capitalization. While ejabberd (the XMPP server we're using) accepted that value, it doesn't support capitalized booleans and hell broke loose when a code path accessing such a configuration option got executed. For one option (like: "ejabberdctl room conference.host logging True") this does cause the XMPP MUC room the option got applied for to get completely deleted immediately. This resulted in the lobby not being available anymore. Debugging what happened took some time. As a workaround we're now passing the configuration values as strings in the first place, which ensures the capitalization stays as desired and doesn't trigger that behavior anymore. I've also opened a bug report for ejabberd, so hopefully it won't be possible in future anymore to set such invalid options: https://github.com/processone/ejabberd/issues/4337.