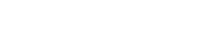Dizaka
Balancing Advisors-
Posts
487 -
Joined
-
Last visited
-
Days Won
5
Everything posted by Dizaka
-
Are you aware of the scale of DoS attacks?
Dizaka replied to badosu's topic in Game Development & Technical Discussion
Problem is the VPN uses the original IP. If DDOSer has original IP and you did not change original IP then DDOSing the original IP will knock out your VPN connection. Though I believe you know that but just putting it out there. VPN doesn't solve everything. VPN is good for being a client. But as a client your IP isn't compromised unless you host. -
Are you aware of the scale of DoS attacks?
Dizaka replied to badosu's topic in Game Development & Technical Discussion
Highly likely the attacks are manual with the person idling in chat on one of the accounts. I believe game time vs idle time in the multiplayer lobby should be monitored. Players who have extensive idle time in relation to games should be kicked and/or banned from lobby. I mean like 12-24 hrs online without starting and/or playing a game. Maybe this could be "nullified" if players are vetter somehow such as the application to be a dev/contributor. Around/after 10:00 pm U.S. Easter Time a lot of this subsides and you can play games. This sort of supports the theory that the attacks are manual. Additionally, the attacks are dynamic. When the attacks are not working different types of attacks are utilized. There are the standard ICMP/UDP packet attacks and they have sometimes been switched to NTP attacks. -
Are you aware of the scale of DoS attacks?
Dizaka replied to badosu's topic in Game Development & Technical Discussion
Do not split community with different lobbies ;/. A lot of players in 0ad but not enough for multiple multiplayer lobbies. -
Are you aware of the scale of DoS attacks?
Dizaka replied to badosu's topic in Game Development & Technical Discussion
To an extent this won't work if your ISP provides a public IP. DDOS is performed on all/random ports. Goal is to choke the pipe to prevent any bandwidth from getting out. It's a sufficient choke of the bandwidth to bring down a 200 mbit connection. @aixo -
Are you aware of the scale of DoS attacks?
Dizaka replied to badosu's topic in Game Development & Technical Discussion
^ -
Had a lot of experience with this around late August and early September. Only time I get DDOS/latency/connection issues is after/during launching 0ad. It had happened when chatting aggressively with other players. Either DDOS person was reading/policing chat or on receiving end of aggression and didn't like it. (Edit: Aggression was a response to being ddosed multiple times previously and trying to figure out if it is a player element or a 0ad element. It's definitely a player/griefer and not the game.)
-
Could be also based on majority votes or rank-based-voting. For rank-based-voting if something is tied the final two items get another vote. If no winner a vote until agreement in chat is reached. There could also be votes for "default" settings since I believe that 90% of the games are default setting games (200 pop, mainland, no relics, conquest victory, etc.).
-
@mysticjim even called @Dakara as @Dizaka liberally and interchangeably in one of his videos! @BoredRusher generally, if everyone disconnects, the host is on the receiving end of the DDoS. There are different levels of attacks that the attacker does. Small attacks to make you lag so that host boots/kicks you. Maybe you're annoying enough to them. Larger attacks to make your connection seem unstable. You can drop from game. You could be pushing the right buttons. Even large attacks if you anger particular players. You likely will drop from game and/or unable to access internet for 2-5 mins. At this point DDoSr is emotionally invested. Largest attack has been about a 25-35 min disconnection from the internet on commercial-grade equipment using a 200mbit connection. Probably because the DDoS'er has no emotional self control. Attacks on host to disconnect everyone. Maybe because they wanted to get in on a game but don't want to wait for one to end? Random night attacks. My guess whoever does this has a script running through IPs at night to agitate other players with blind shots. This could be just to deflect attention from them and onto players for "having bad internet connections." Interestingly, there's a limited number of players in lobby mocking others for "crappy internet." The only way to stop attacks, from my perspective, is through 'bot hosts' hosted on Amazon, Azure, or some other cloud service with DDoS protection who rejoin the 'lobby' upon disconnections so players can rejoin. This protects players from joining hosts of compromised players who do those attacks (therefore, they can't get new IPs). Additionally, this prevents someone from lobby getting the host IP addresses (player IP addresses) and, instead, getting a cloud IP address that has the counter measures necessary to alleviate the DDoS. In general, 0ad has GOOD network code and a majority of players have GOOD connections. The issue is some dumbass from the community ruining it for others pretending he has a NASA host. In the end your realize it's a child with a lot of growing who is afraid to reveal who they are. Finally, whoever does this has interesting control over the attack. I've noticed two ways attacks are done: Large packets being sent to you. Tons of small packets being sent. I haven't setup Wireshark but there are players who have (who, actually, professionally do telecom) agree that it is a DDoS. @BoredRusherAlso, not saying it's berhudar (could be someone else if Wolo has static/same ip) but worth cross-checking IP his addresses with those of other players and also checking if he plays behind a proxy. An admin maybe could do that.
-
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
3:55 pm eastern US time. Internet was down (per ISP device being restarted as managed by Switch). Short downtime that I didn't realize happened. -
/ban help /ban add <playername> /ban remove <playername> /ban list /ban auto <on/off> (Bans could be a blacklist to prevent certain friends from joining games. Alternative to 'ban list' could be having other than a "friends" list such as a "watched players" list)
-
When playing 0ad whole network disconnects. Network otherwise stable.
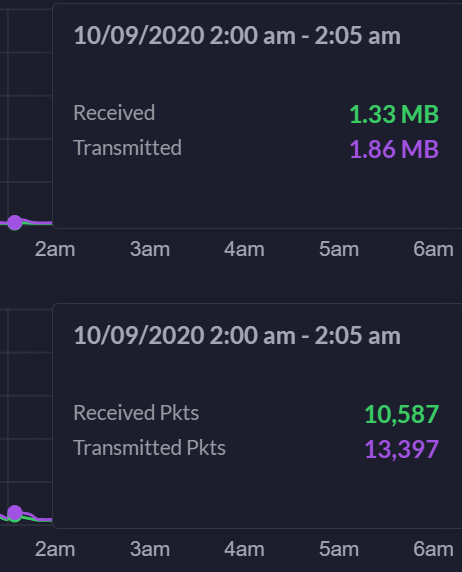
Dizaka replied to Dizaka's topic in Gameplay Discussion
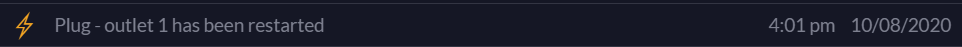
10/9/2020 @ 2:05 am US eastern time (Was sleeping, no games/replays). WAN port: LAN: Looking at last 2 mos of traffic logs latency at 2:05 am, or so, is not normal [Edit: wrote wrongly]. Currently, over last few days, when playing 0Ad (2-3 games?) or during daytime no issues. -
It's hard to read for a non-native English speaker who knows basic English. If he could write differently it would be significantly easier for others to go through the text. However, for a native English speaker going through that doesn't really matter as it is straight forward. I think a lot of people fail to understand that because a lot of people here are bi-lingual then English isn't a primary language, more of a common language. I thought Boudica, and a number of other players, are native English speakers but they surprisingly aren't. I don't think Vinme is using 133tsp34k. Instead, he's using the English he's self-taught or gotten through the internet. Posting on a msg board for a non-native could be viewed as learning. IMO, learning should have constructive feedback and not negative feedback. Otherwise you'll just end up agitating and/or making the other person angry. There was plenty of that in 1997. Shouldn't be happening now. Anyway, that's just my opinion.
-
When playing 0ad whole network disconnects. Network otherwise stable.
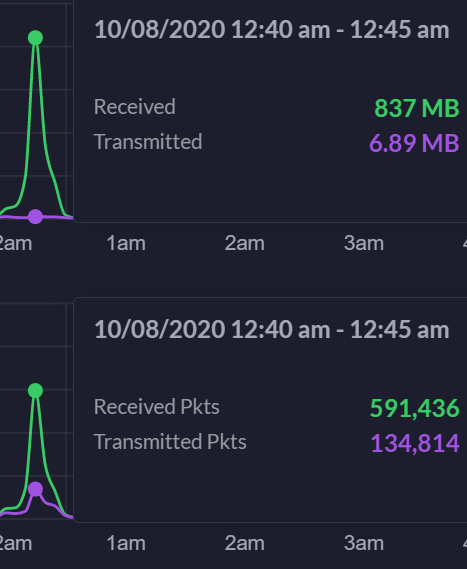
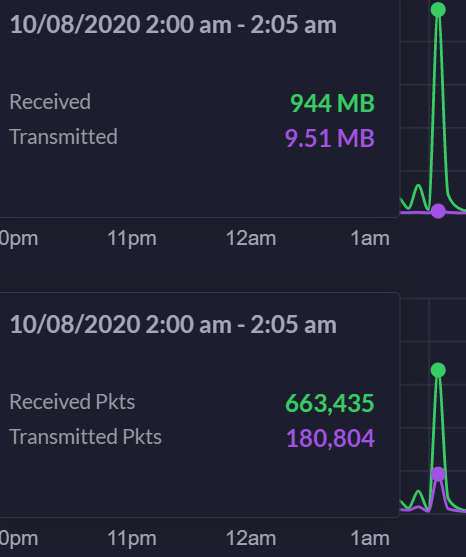
Dizaka replied to Dizaka's topic in Gameplay Discussion
Apparently two DDoS attacks happened at night. At least highly unusual logs. 10/8/2020 @ 12:40 am. 10/8/2020 @ 2:00 am. I thought DDoS' attacks are intended to disrupt service and anger people? These done at night impact me so much that I realize after the fact that they happened. lulz. -
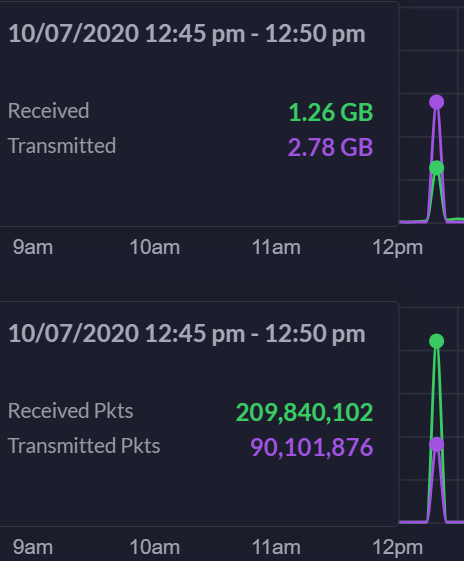
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
10/7/2020 @ 12:50 pm. Wasn't doing anything and didn't even realize it happened but it's there in the logs. LOL. What's interesting is the attacks are now asking my router to send back data ... -
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
There isn't much that can be done. This post is more about showing that there is an issue and that there are bad actors. We don't even know what the motivation is behind these bad actors. Is it to end games so that they can play 0Ad (lulz)? Is it to grief players (2x lulz)? It is unknown. Mostly b/c the actors are covert and not overt. The people doing this are afraid of any RL repercussions, otherwise they'd post their personal information. In conclusion, I will actually defend the devs and all the volunteers. They are doing an amazing job with this game and I wouldn't be posting here if they weren't. The person doing the DDoS is just going to DDoS. DDoS'r, please spend more $$ on your DDoS or get some skillz. -
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
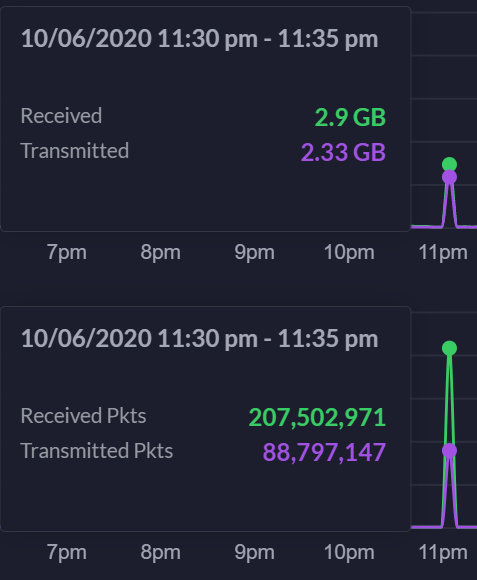
11:30 pm or so on 10/6/2020. While in bed tablet device wasn't connecting to internet (WiFi was working). I guess this explains why I fell asleep earlier last night. Attacks are pretty boring and old now. In any case, DDoS'r - can you do this more often at 11:30 pm, or so? I got some good sleep and this is helping my insomnia. Anyway, #gohardorgohome. Waiting for that ISP phone call. -
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
Before last DDoS it appears Borg and Chetnik also got DDoSed. Note, 9:00 pm and I think DDoS has subsided. -
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
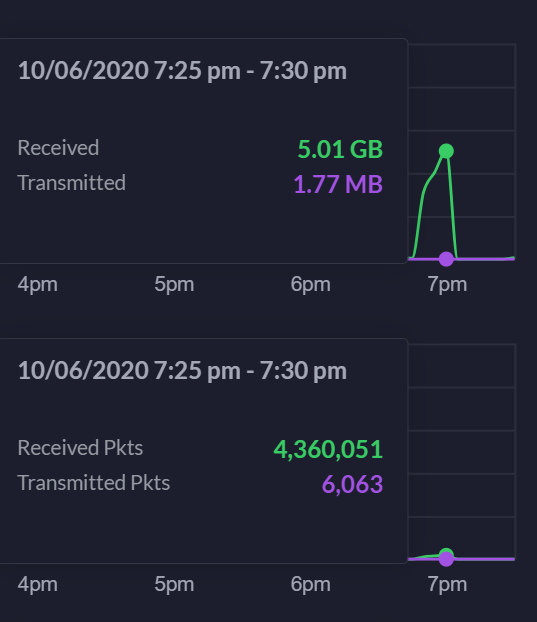
7:20 eastern time. Ddosed as a player. Will update as time progresses. 7:41 pm, still offline on that WAN port. 7:50 pm. Still offline. 7:55 pm, or so. DDoS ended. -
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
-
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
Found something weird going through logs. Could be relevant or could be not relevant. Threat Management Alert 2: Potentially Bad Traffic. Signature ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)). From: A.B.C.D:53180, to: 104.31.64.171:80, protocol: TCP 3:55 pm 09/23/2020 Threat Management Alert 2: Potentially Bad Traffic. Signature ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)). From: A.B.C.D:53084, to: 104.31.65.171:80, protocol: TCP 3:54 pm 09/23/2020 Threat Management Alert 2: Potentially Bad Traffic. Signature ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)). From: A.B.C.D:52919, to: 172.67.180.106:80, protocol: TCP 3:53 pm 09/23/2020 Threat Management Alert 2: Potentially Bad Traffic. Signature ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)). From: A.B.C.D:52909, to: 216.105.38.13:80, protocol: TCP Threat Management Alert 2: Misc Attack. Signature ET CINS Active Threat Intelligence Poor Reputation IP group 21. From: 45.129.33.81:41427, to: A.B.C.D:20595, protocol: TCP 9:50 pm 09/19/2020 Threat Management Alert 2: Misc Attack. Signature ET DROP Dshield Block Listed Source group 1. From: 45.129.33.81:41427, to: A.B.C.D:20595, protocol: TCP 9:50 pm 09/19/2020 The bad IP addresses: 104.31.64.171 172.67.180.106 216.105.38.13 45.129.33.81 Odd thing is that here: Threat Management Alert 2: Misc Attack. Signature ET DROP Dshield Block Listed Source group 1. From: 45.129.33.81:41427, to: A.B.C.D:20595, protocol: TCP 9:50 Specifically the 20595 port is being addressed. That's the 0Ad game port. Look here: https://www.dshield.org/block.txt . The IP is on the Dshield.org website ... I guess abuse@ipvolume.net is getting an email. 1954 indicates that the 45.129.33.0 address group is a Canada and/or Fort Lauderdale regional ownershipo. Edit: Ooops. Country code is from Seychelles, East Africa. Code is 2047 for 45.129.33.*. Not sure where 1956 came from. -
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
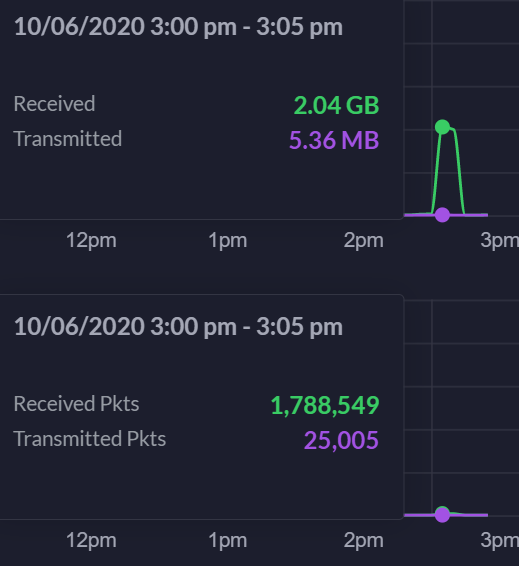
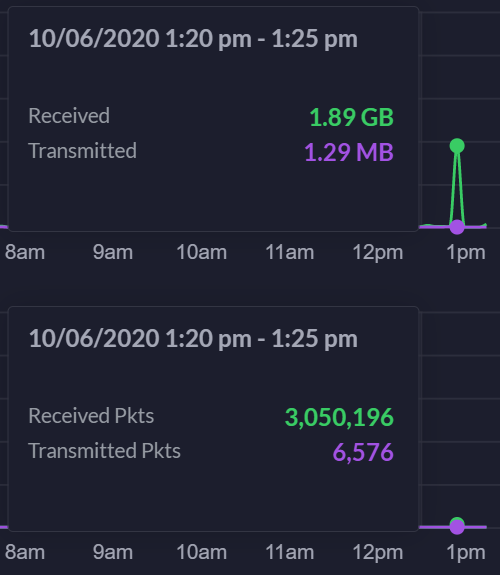
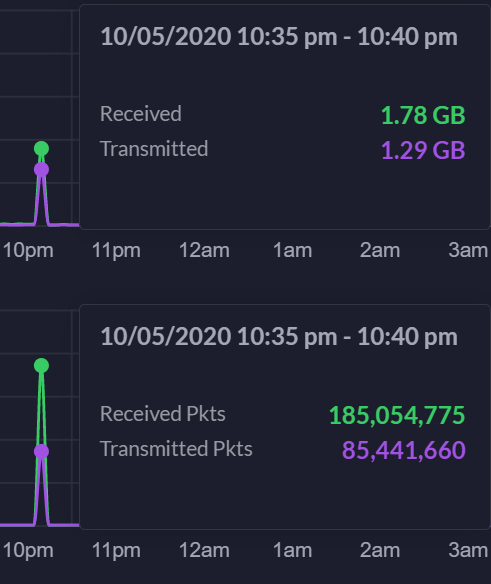
10/6/2020 around 1:23 pm Eastern Time. Clearly hit a nerve with someone through my last post. Internet/0Ad WAN port down due to DDoS. 1:36 pm. Whoever is doing this #gohardorgohome. My ISP hasn't called yet. 1:41 pm. It stopped. Chart is below. What's interesting is whoever is doing this is optimizing the attack. I've noticed that they are starting to send more packets now but lower bandwidth utilization. For example, see below: 185,054,775 packets received. That's like 100x higher than usual. Therefore, whoever is doing this is trying to, using what some people call a brain, to optimize the attack. -
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
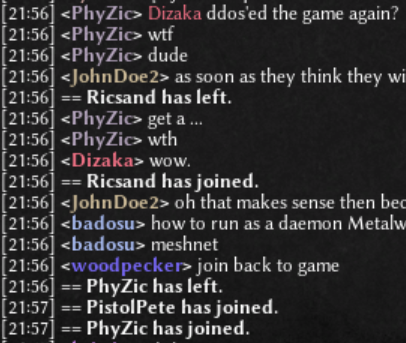
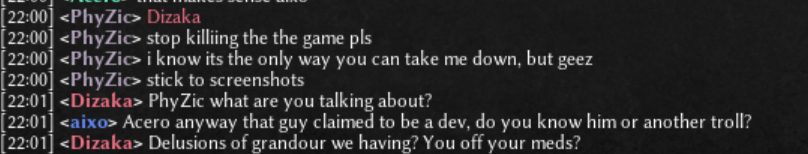
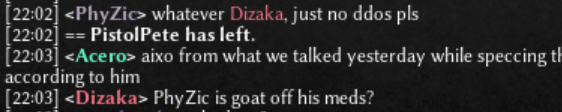
Not sure. The person is being more covert than overt. Like as if they were afraid of repercussions for their actions. Like as if they didn't have a pair (male or female pair, either of the the two or both - I don't judge). Total wussies. Edit: Apparently there is at least one person who has the audacity to allege that I'm the DDoSer who ruins games. See below (General Lobby Chat from 10/5/2020, eastern time zone): -
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
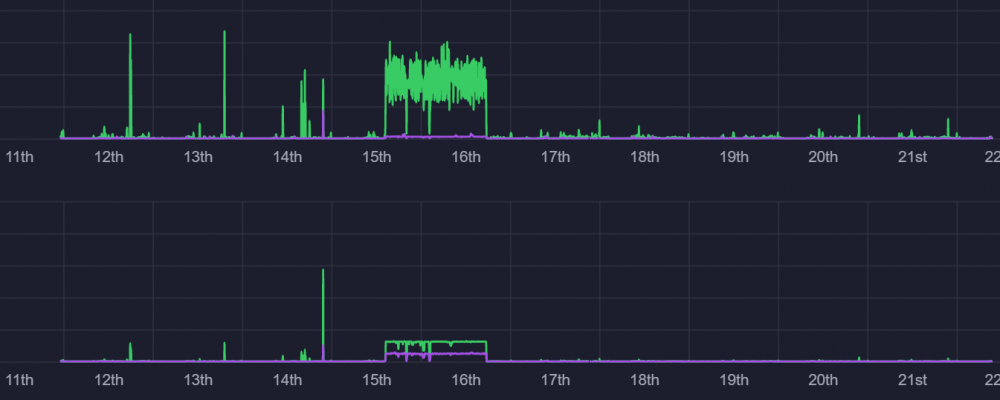
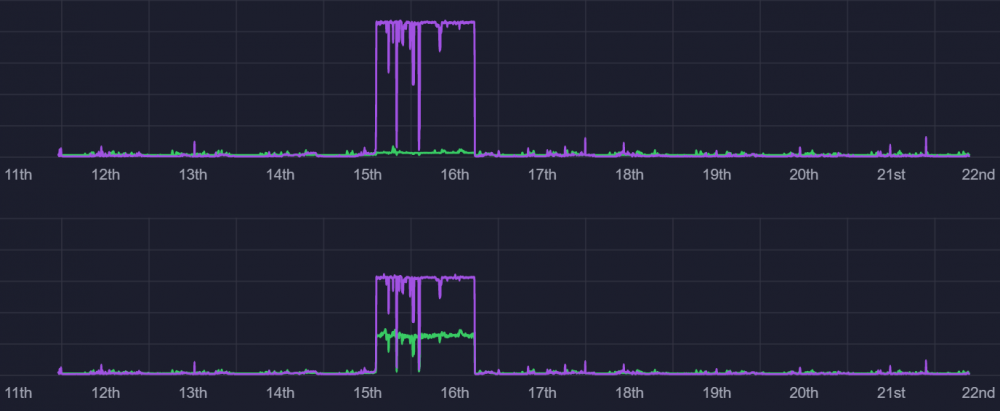
On 10/5/2020 between 9:00 pm and 11:00 pm eastern time the lobby users are being hit hard by who ever is the DDOS child. I'm being ignored for some reason. Mgically, a number of users who rarely, if ever, log in logged in. The first topic on these user's mind was DDOS. Peculiar but just speculation. Below is a WAN chart of traffic since 9/11. Most peaks, if not all, except between 9/15 and 9/16, are when I disconnected from 0ad due to, what I believe, were ddos attacks. Below is the corresponding LAN chart. Notice how traffic between 9/15 and 9/16 can be seen on LAN? That's because it goes past the router and isn't blocked/discarded like a DDOS attack. The 9/15-9/16 traffic is a 4 tb download. -
When playing 0ad whole network disconnects. Network otherwise stable.
Dizaka replied to Dizaka's topic in Gameplay Discussion
Just did a quick search for DDOS on the forum. Looks like this has happened with players who get singled out. Example is Emperior: Not really an issue to ignore. I also haven't seen Emperior around.